Instant isolation
Launch hardened sandboxes in seconds, each with strict resource limits and clean workspaces.
- Per-sandbox CPU/RAM limits
- File operations + exec streaming
- Fast terminate + cleanup

Spin up isolated sandboxes in seconds, run code safely, and pay a fraction of typical prices. Designed for AI agents, build systems, and modern dev teams that refuse to overpay.
Drop in an API key, create a sandbox, and execute code safely. No infra burden.
Why Sandy
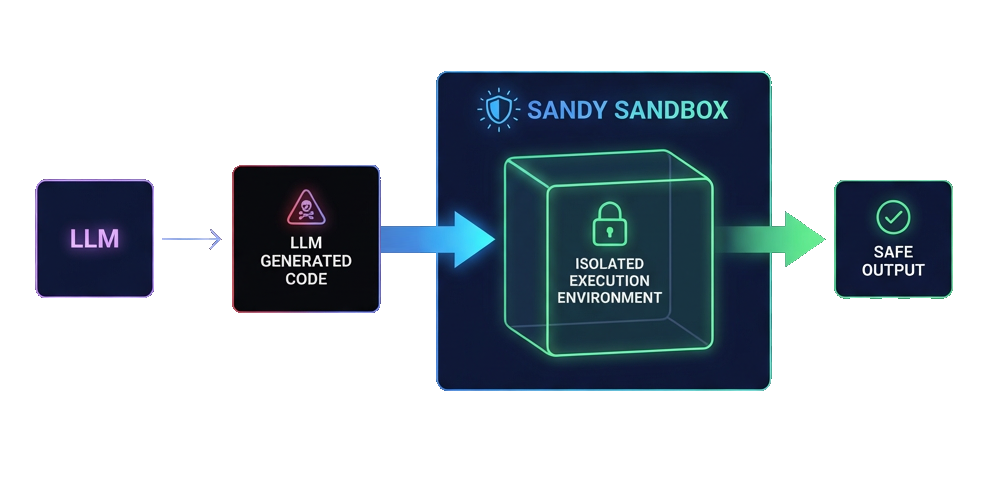
Sandy protects both AI-generated code and autonomous agents at scale.
Models can produce helpful code, but they can also introduce risk. Sandy keeps execution isolated, captures output, and prevents surprises in production.
Agents are most efficient when they can run without constant approvals. By giving each agent a hardened sandbox, Sandy unlocks YOLO mode while staying secure and scalable.
Create a sandbox in one call, stream output, and terminate cleanly.
Platform
Sandy is purpose-built for AI coding workflows and massive parallel test runs. Every sandbox includes deterministic build environments, shared caches, and low-latency IO.
Launch hardened sandboxes in seconds, each with strict resource limits and clean workspaces.
Reuse dependencies and datasets across sandboxes. Dramatically cut build times and bandwidth.
Run CLI agents, compilers, and browsers inside the sandbox without fragile orchestration.
Works with your existing LLM pipeline and CI tools.
curl -X POST https://sandy.sandbox-as-a-service.com/api/sandboxes \
-H \"Authorization: Bearer $SANDY_API_KEY\" \
-d '{\"enable_docker_socket\": false}'
curl -X POST https://sandy.sandbox-as-a-service.com/api/sandboxes/sb_72b4/exec \
-H \"Authorization: Bearer $SANDY_API_KEY\" \
-d '{\"command\": \"node --version\"}'API docs
Authenticate once, spin up sandboxes, stream output, and ship.
Send your Sandy API key as a bearer token on every request.
Authorization: Bearer $SANDY_API_KEYAdvantage
Sandy runs on dedicated, optimized infrastructure. We pass the savings directly to teams that want reliable sandboxes at scale.
Up to 95% lower sandbox cost
From $5 per sandbox / month for entry usage.
20 always-on sandboxes, monthly estimates:
Price comparison uses 20 sandboxes for one month across providers.
Pricing
Start small, scale into multi-region fleets, and keep every sandbox under control.
From $5/month
Smallest config: 0.5 vCPU / 1 GB RAM. 1 vCPU / 2 GB RAM is $20.
Custom/month
Let’s talk
Security
Every sandbox is locked down by default. You can opt into elevated permissions only when you need them.
CAP drop, no-new-privileges, and strict resource controls.
Outbound controls, per-sandbox host suffixes, and private ingress routing.
Telemetry events stored in Postgres with export-ready history.
FAQ
Cold start is typically 2-4 seconds. Prewarming can reduce this further.
Yes. The runtime ships with optional Playwright + Chromium builds.
Yes. Enterprise plans support custom runtime images and internal registries.
Ready to replace expensive sandbox providers with a modern, efficient stack?